Getting Started with Azure Active Directory Premium for Cloud Solution Providers
Introduction
The Microsoft Cloud Solution Provider (CSP) program was released in July 2014 to provide a scalable, flexible partner program. Designed to deepen customer relationships and expand business opportunities, the CSP program allows partners to:
- Own and control billing
- Sell combined offers and services
- Deliver direct provisioning, management, and support
To achieve those capabilities, CSP partners need to integrate their backend systems and business processes with various Microsoft cloud services and processes. Once integration has taken place, CSP partners then have the ability to directly provision, manage and support clients within the Microsoft Office 365, Microsoft Azure, Dynamics CRM, and Enterprise Mobility Suite (EMS) product offerings.
The goal of this document is to help CSP organizations to quickly implement Azure Active Directory Premium, part of the Enterprise Mobility Suite , as a solution for their clients.
This document provides guidance on how to gather necessary information from clients to facilitate the initial setup of Azure Active Directory Premium. It also provides step by step instructions on how to configure its various features.
Scope
The scope of this document is to provide implementation and configuration guidance for the following Azure Active Directory Premium features:
- Self-Service Password Reset
- Delegated Group Management
- Dynamic Group Access
- Azure Active Directory SaaS applications
Terminology
Before you start
This document assumes that the following conditions have been met:
- The steps in the document "Getting Started with the Office 365 and EMS for Microsoft Cloud Solution Providers" have been completed
- Password write-back has been enabled in Azure Active Directory Connect
- The administrator completing these steps has co-administrator access to the Azure subscription
- All users have authentication contact attributes associated with their user account, i.e. authentication phone, alternate authentication phone, or authentication email
Configuring Self-Service Password Reset
Azure Active Directory Premium's self-service password reset function grants end customer user the ability to reset their own passwords without the need to engage the services of an IT administrator. Before implementation, there are number of elements to Self-Service Password Reset that need to be agreed upon with the end customer.
Gathering end customer Self-Service Password Reset requirements
The following table outlines the features and functions that need to be agreed upon with the end customer to allow the CSP Partner to proceed with the configuration of Self-Service Password Reset.
CSP Partners can leverage this table to discuss and determine end customer settings for each of the Self-Service Password Reset configuration options.
For more information, refer to the document Customizing Password Management to fit your organization's needs.
Configuring end customer Self-Service Password Reset requirements
- When the requirements have been gathered from section 3.1, sign in to the Azure Management Portal as a co-administrator for the end customer tenant.
NOTE: If you experience an issue while logging into the Azure Portal as a partner with the customers Azure Active Directory (AAD) subscription, and see your own tenant and not the end customer's tenant, allow the browser session to completely load and then sign out and log in again to access the correct tenant.
- Select the AAD tenant for the end customer:
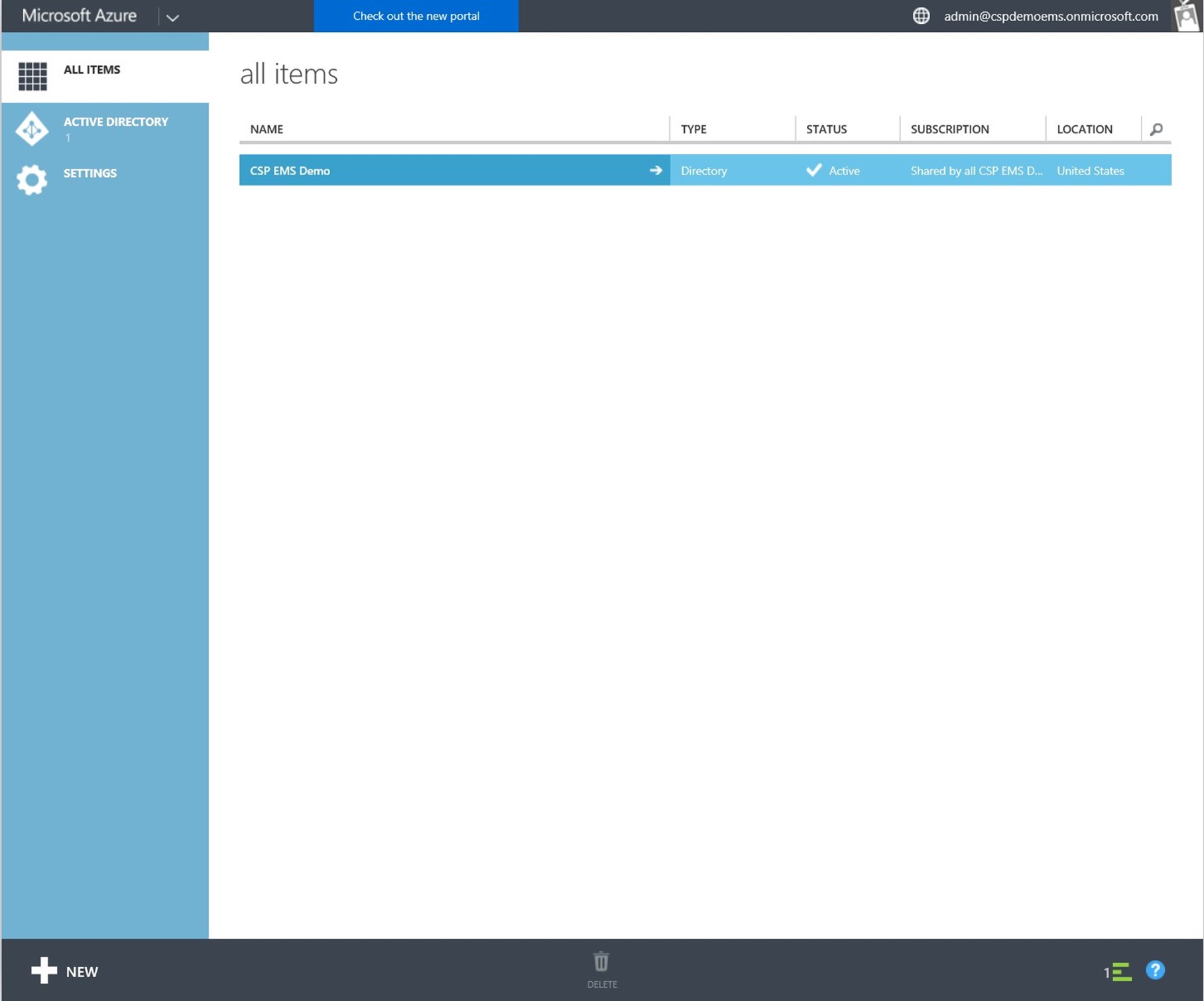
- Select the CONFIG tab.
- Under the heading, user password reset policy, select YES for USERS ENABLED FOR PASSWORD RESET to enable self-service password reset.
- The User Password Reset Policy will populate will the configurable options:

- Complete the configuration according to the information gathered from the end customer.
- Once complete, select SAVE.
Configuring group management
Delegated group management
Azure Active Directory Premium's group management function grants the ability to delegate group management to the end customer users. With this feature, end customer users are able to create and manage memberships in groups they own. There are number of elements to group management in AAD that need to be agreed upon with the end customer.
The following table outlines the features and functions that need to be agreed upon with the end customer to allow the CSP Partner to proceed with the configuration of group management.
| Group Management Option | Description | End Customer Setting |
| Delegated group management enabled | Enable delegated group management for users through the access panel | Yes |
| Users can create security groups | Enable users to create new security groups through the access panel | Yes/No |
| Users who can create security groups | Select "some" to restrict security group management to only a limited group of users | All/Some |
| Group that can use selfservice for security groups | Defines the group of users who are allowed to create security groups | Enter AD Group Name: ______________________ |
| Users can create Office 365 groups | Preview Feature Enable users to create new Office 365 groups through the access panel | Yes/No |
| Users who can use self-service for Office 365 groups | Restrict management. Select "some" to restrict Office 365 group management to only a limited group of users. | All/Some |
| Group that can use selfservice for Office 365 groups | Defines the group of users who are allowed to create security groups | Enter AD Group Name: _________________________ |
| | | |
| Enable dedicated groups | Select "yes" to enable dedicated groups in the directory | Yes/No |
| Enable "All Users" group | Select "yes" to enable the All Users group in the directory. | Yes/No |
| Display name for "All Users" group | | Default: All Users Enter Group Name: __________________________ |
- When the above information has been gathered, sign in to the Azure Management Portal as a co-administrator for the end customer tenant.
- Select the AAD tenant for the end customer:

- Select the CONFIG tab.
- Scroll down to group management.
- The user password reset policy will populate will the configurable options:

- Complete the configuration according to the information gathered from the end customer.
- Once complete, select SAVE.
Dynamic group membership
The following section provides an example scenario where group membership within AAD can be established dynamically, based on user attributes synchronized from on-premises user properties.
This example will dynamically add marketing users to the Twitter AAD group.
This group will then be used in section 5 to assign Software-as-a-Service applications to users.
- From within the Azure Management Portal, select the AAD tenant for the end customer:

- Select the GROUPS tab:

- Select ADD A GROUP.
- Enter the following information:
| Field | Description | Value |
| Name | Friendly name of the group | |
| Group type | Select the group type for this group | Security |
| Description | Use this field to describe the group's purpose, members, or access type that would be granted when a user becomes a member | Twitter for Marketing |
- Click the tick button to create the group.
- Once the group has been created, select the group to view the properties.
- Select the CONFIGURE tab:

- Under the dynamic membership tab, select YES to ENABLE DYNAMIC MEMBERSHIPS.
- Select YES to the warning popup:

- Build the ADD USERS WHERE membership query with the following information:
| Radio Button | Drop-down Menu | ||
| Add Users Where | Department | Equals (-eq) | Marketing |

- Select SAVE. All users with the Active Directory attribute Department with Marketing as a value will be dynamically added to the group.
- Review any dynamically assigned members of the group by selecting the MEMBERS tab in the Twitter Group menu:

Configuring Software-as-a-Service applications
AAD integrates with thousands of Software-as-a-Service (SaaS) applications. CSP Partners will want to provide end customers with access to SaaS applications managed by AAD.
Review the list of available applications at the Azure Active Directory Marketplace
with the end customer, including any designated as a CSP Partner who are included as part of the offering to the customer.
Once the appropriate applications for the end customer have been agreed upon, these can be added to AAD to provide managed and secure access to SaaS applications.
Adding Active Directory SaaS applications
In this example, the following instructions will add Twitter to AAD as a managed application for the end customer. This Twitter SaaS application will integrate with the dynamic group created in the previous section of this document to define which end customer users can gain access. Additionally, as the application is managed, each of the end customer users, defined in the dynamic group, will be logging in with a single Twitter for Marketing account, and therefore will not require individual usernames and passwords for access.
- Sign in to the Azure Management Portal as a co-administrator for the end customer tenant.
- Select the AAD tenant for the end customer:

- Select the APPLICATIONS tab.
- There will be applications provisioned automatically as part of the EMS and any Office 365 subscriptions:

- Select ADD.
- Select Add an application from the gallery:

- Enter Twitter into the search field and select the search icon.
- Enter the display name of the application as Twitter for Marketing:

- Click the tick icon to continue. This will add Twitter for Marketing to the list of managed AAD applications.
- The properties of Twitter for Marketing will now be displayed:

- Select Assign accounts.
- Enter within the search field the word, Twitter, and tick the box to continue.
- A list of all AAD groups with the word 'Twitter' will be displayed.
- Select the Twitter group and select ASSIGN:

- A window to configure the authentication for the SaaS application will appear.
- To configure a shared account for the SaaS offering that is managed by the administrator, enter the following values:
| Setting | Description | Value |
| I want to enter credentials to be shared among all group members | Administrative populated credentials without the need to provide individual users with the authentication details | Selected |
| User name | | Application user name |
| Password | | Application password for user name provided above |
| I want to enable auto password rollover | Refer to Azure Active Directory enables automatic password change for shared accounts for further details | 1-13 Weeks During each password update, the password is updated using a randomly generated 16- |
| character complex string. To disable this feature and regain normal access, you will need to go through the password reset procedure provided by the application. |

- Select the arrow to continue.
- Select the Rollover Frequency:

- Click the tick box to continue.
This process can be repeated for any other SaaS applications that are to be integrated with AAD for the end customer.
For tutorials related to other AAD integrated SaaS applications, refer to the Azure documentation List of Tutorials on How to Integrate SaaS Apps with Azure Active Directory.
Reference links
- CSP Partner Center Portal http://partnercenter.microsoft.com
- Azure Management Portal https://manage.windowsazure.com
- Azure Administration Portal https://portal.azure.com
- Customizing Password Management to fit your organization's needs https://azure.microsoft.com/enus/documentation/articles/active-directorypasswords-customize
- Password Writeback https://azure.microsoft.com/enus/documentation/articles/active-directorypasswords-getting-started/
- Active Directory Marketplace https://azure.microsoft.com/en-us/marketplace/activedirectory
- List of Tutorials on How to Integrate SaaS Apps with Azure Active Directory https://azure.microsoft.com/enus/documentation/articles/active-directory-saastutorial-list
- Azure Active Directory enables automatic password change for shared accounts https://azure.microsoft.com/en-us/updates/azureactive-directory-enables-automatic-password-changefor-shared-accounts
- Connect to Office 365 PowerShell https://technet.microsoft.com/library/dn975125.aspx