Share protected content with Azure Rights Management
Introduction
Every day, information workers use e-mail messages to exchange sensitive information such as financial reports and data, legal contracts, confidential product information, sales reports and projections, competitive analysis, research and patent information, customer records, employee information, etc.
Ever more powerful devices, converging technologies and the widespread use of the Internet have replaced in mobility situation what were (controlled and managed) laptops in past years. Today, information workers are highly interconnected and, with the consumerization of IT, more and more of them are using the device of their choice to access e-mails and work-related documents from just about anywhere. This raises new challenges for security. With the time, the type, volume and sensitivity of information that is exchanged has changed significantly. Mailboxes have transformed into repositories containing large amounts of potentially sensitive information. Furthermore, as of today, information workers are not just more mobile than ever before, but they are also more demanding on external collaboration. Users indeed expect to be able to collaborate seamlessly with any business user not only within the organization but also outside.
Considering the above, information leakage can be a serious threat to organizations. Leaks of confidential information can result in lost revenue, compromised ability to compete, unfairness in purchasing and hiring decisions, diminished customer confidence, and more. Consequently, IT needs to make sure that proper policies and technologies are in place with specifically the ability to protect and control access to sensitive corporate files from:
- A broad base of the internal employees.
- A collection of organizations or individuals the organizations and/or the information author choose to collaborate with.
- Various exposure risks data is subject to notably when stored on non-managed devices, or in the cloud.
Each of these capabilities poses different challenges. These challenges demand effective Information Protection and Control (IPC) systems, which are not only secure but are also easy to apply, whether it's to e-mail messages sent or documents (of all types) accessed from various devices, inside an organization or outside the organization to business partner organizations/individuals.
Note IPC is also known as a different set of names including: data leakage prevention, data loss protection, content filtering, enterprise rights management, etc. All of these categories aim to prevent an accidental and unauthorized distribution of sensitive information.
Protect is « Prove who you are » before granting access. The document is unlocked (in fact decrypted) if the user is authorized to access it. Control is « limit the usage of the information ». Control goes a step further by granting people access while removing their abilities (for example, to edit, copy, or print) in accordance to usage policy.
One should note that IPC is available for more than a decade but only few organizations are using this kind of solution. This can be explained by previous lack of interest of Business Decision Makers or by the complexity generally observed when deploying such a far-reaching solution. Also user's expectation is high and they are not tolerating any downtime. Users would not be satisfy if the protected document they are trying to read couldn't be open because an Information Protection element is not responding or if it isn't supported on their devices. Deploying on-premises IPC can be challenging and/or require significant knowledge to be done right. This was notably the case for Microsoft Active Directory Right Management Services (AD RMS), an information protection technology that enables AD RMS-enabled applications such as Microsoft Office to protect digital content from unauthorized use, both online and offline, inside and outside of the organization's boundaries.
Unlike AD RMS, the Azure Rights Management service provides for everyone a Software as a Service (SaaS) information protection solution that work across classic boundaries.
The Azure Rights Management service is included in the Office 365 Enterprise E3 and E4 plans. It can also be purchased as a standalone with these plans: Office 365 Enterprise E1, Office 365 Enterprise K1, Exchange Online Plan 1, Exchange Online Plan 2, and Exchange Online Kiosk.
The Azure Rights Management service can be purchased standalone for use with the on-premises infrastructure thanks to Rights Management connector.
As a highly scalable and available cloud-based IPC solution run by Microsoft in data centers strategically located around the world, the Azure Rights Management service enables organizations of any size to minimize the effort required to implement an effective IPC to sustain the collaboration inside and outside of the organization's boundaries.
Regardless of how the Azure Rights Management service is purchased by organizations (Office 365 SKUs or stand-alone SKU), by leveraging Azure Active Directory (Azure AD), the Azure Rights Management service acts as a trusted hub for secure collaboration where one organization can easily share information securely with other organizations without additional setup or configuration.
In this context, Microsoft RMS enlightened applications along with the Microsoft Rights Management sharing applications enable users to share protected content with any file format not only on computers but also on most popular mobile devices. The user experience is fast and straightforward.
As of today, information workers are not just more mobile than ever before, they also more demanding on external collaboration. Thus, users expect to be able to collaborate securely with any business user even those who don't have signed up yet for the Azure Rights Management service. Thanks to the free Microsoft Rights Management for individuals, anyone can sign up for Azure Rights Management service and start collaborating on protected documents.
Objectives of this paper
This document provides information about Microsoft RMS enlightened applications and how they can be used to share and collaborate on sensitive corporate data. This paper also presents the Microsoft Rights Management sharing application that are available on all important devices.
Furthermore, by following the steps outlined in this document you should be able to share with anyone (any business user or any individual) thanks to the free Microsoft Rights Management for individuals offer.
Non-objectives of this paper
This document doesn't offer a full description of the Azure Rights Management service offerings. It rather simply focusses on key aspects in the context of this paper that aims at providing the readers an understanding on how to collaborate with anyone on all important devices.
Note For an overview of the NEW Azure Rights Management services offerings, see the whitepaper Azure Rights Management services, the online documentation as well as the posts on the RMS Team blog.
Organization of this paper
To cover the aforementioned objectives, this document is organized by themes, which are covered in the following sections:
- Sharing on Computers and all important devices
- Sharing with anyone
About the audience
This document is intended for IT professionals and system architects who are interested in understanding the various options for protecting and controlling information assets in their environment based on the Azure Rights Management service's foundation and how to leverage the related capabilities.
Sharing protected content on computers and all important devices
The proliferation of consumer devices (smartphones, tablets and PCs) and ubiquitous information access is driving the organization to define a new model in which employees use their own devices to access sensitive corporate data. The model must be flexible enough while at the same time guarantees that sensitive corporate data are protected from unauthorized access regardless whether the user's device is managed or not, etc.
To increase productivity, users ask for a secure and consistent way to access and share sensitive information from their devices.
Microsoft is delivering a solution on all important devices through the Azure Rights Management service. The Azure Rights Management service gives the capacity to make sensitive corporate information available to users on all important devices while protecting information during storage or in transit. Dispersed enterprise data can now be protected in a consistent way.
Once a document is protected, even if it is copied on a USB Key, stored on your laptop or on your mobile device, stored in any cloud provider's storage of your choice, the document carries the same protection. The protection travels with the information whether it has been protected either locally or in the Cloud.
In other words, with the Azure Rights Management service, you can ensure that encryption is implemented for data-at-rest, data-in-transit and data-in-use (encryption-in-use is a capability that must be included in the application processing the data).
The Azure Rights Management service goes further than classical encryption technology by adding policies. That why, the Azure Rights Management service is fundamentally an effective Information Protection and Control (IPC) solution. One should stress that the Azure Rights Management service never has access to the data. The Azure Rights Management service is file transport and file storage agnostic. It operates on (all type of) files only when they are 'activated' (protected, opened/consumed) as notably described later in the next section.
Leveraging the Microsoft RMS enlightened applications
As time evolves, users now want to access corporate data (e-mails, Office documents, PDF documents, pictures, etc.) from anywhere from their devices. They also want a consistent user experience to access sensitive data from their devices, including a simplified sign-on process when accessing such information.
On should note that accessing or sharing a protected document is best experienced within an RMS enlightened application.
RMS enlightened applications enable individuals to protect and consume content. Content is protected by using encryption and must be decrypted before it can be consumed. When the file is protected, the individual applies permissions to the file such as the ability to print or edit. The application will need to honor these rights.
Such an application leverages for that purpose the RMS SDK 2.1 and above. The RMS SDK facilitates most of the protection flows and all initialization. It indeed takes care of all the underlying details about the environment and topologies, document expiration, certificate renewals, policy updates and more. Furthermore, if the application must honor the permission enforcement requested of it, the SDK makes enforcing the rights easier by providing APIs to control permissions such as printing, saving, forwarding, etc.
Note For additional details on permissions, see the MSDN articles AD RMS developer concepts and Built-in Rights Usage Restriction Reference.
The RMS SDK protects the data within the runtime environment they are executing. This is normally a computers (Windows or Mac OS/X) or a mobile device (Windows RT, Windows Phone, iOS, or Android).
Note As of this writing, there is no specific support for Linux or Blackberry. The RESTful API support of the RMS SDK can be leveraged for that purpose. If there's a platform that is missing and you consider critical, then you can contact the product team: askIPteam@microsoft.com
Those runtimes use the RMS SDK to interact with the Azure Rights Management service:
- The Azure Rights Management service, when responding to client SDK requests, is responsible for the secure encryption key interchange with the SDK in order to protect the data without the data going to the Azure Rights Management service.
- Once protected, the Azure Rights Management service plays key roles in document consumption:
- The user must be authenticated. The Azure Rights Management service requests an authorization token from the appropriate identity provider. Generally, this is the on-premises federated identity infrastructure, such AD with AD FS, or the Azure AD organization's tenant as part of Office 365 or as a stand-alone service but support for Microsoft Account (a.k.a. Live IDs) and Google IDs is seek to be introduced.
- The user must be authorized. The Azure Rights Management service serves as a unified policy decision point and a policy enforcement point to follow policies established by your organization. This is done by having Azure Rights Management service process the document policy associated with a protected document and then decide if the recipient should be granted permission to view the document.
- Every use must be logged. All user activity, successful or not, is logged in Azure Rights Management service's logs enabling your IT staff to audit access.
-
Mobile device applications use the new lightweight Microsoft Rights Management SDK (RMS SDK) 4.0with the latest mobile client, and benefit from Microsoft-provided user interfaces for consumption and protection behaviors. This not only saves time to build protection support, but it also provides a consistent protection user experience (UX) as the UX is integrated into the SDK itself.
Note The RMS SDK 4.0 is a simplified, next-generation API that enables a lightweight development experience in building or upgrading device apps with information protection via the RMS service, whether it is an on-premises AD RMS cluster with the mobile device extension or Azure RMS.
Its APIs use standard programming languages and models for each operating system so, they are easy and familiar to work with. The RMS SDK 4.0 provides support in mobile devices (Android, iOS, Mac OS X, Windows Phone, and Windows RT.
For additional information on the RMS SDK 4.0, see the eponym MSDN page Microsoft Rights Management SDK 4.0.
The Rights Management sharing application (see next section) constitutes a good illustration of the UX that the SDK provides.
Windows desktop based RMS enlightened applications utilize the RMS SDK v2.1, which doesn't yet offer built-in consumption and protection flows. (This will change in a near future.)
As of this writing, the following applications and services natively support the Azure Rights Management services:
- Office 365 (protected e-mails messages and PDF and Office documents with Exchange Online and SharePoint Online),
- Office 2013 and Office 2010 (protected e-mails messages (Outlook) and Office (Word, Excel, and PowerPoint) documents).
- Outlook 2013 RT on Windows 8.1 RT (for protected e-mail messages).
- Office Mobile preinstalled on Windows Phone 8 (protected Office documents).
Note Office Mobile for iPhone and Office Mobile for Android are now available for Office 365 subscribers, but doesn't support yet RMS protected Office files
- Foxit Enterprise Reader with the RMS PDF Plug-in Module and Foxit Mobile PDF (protected PDF documents).
Leveraging the Rights Management sharing applications
Microsoft is delivering a cross-platform sharing application that is available on all important devices: the Rights Management sharing application. This sharing application constitutes the easiest way to shared protected content across computers and important devices without compromising the security.
This sharing application is available on computers (Windows and Mac OS/X) and also on the most popular mobile devices (Windows RT, Windows Phone, iOS, and Android).
The sharing application can be download from the Microsoft Rights Management Download Center: Windows Desktop, Window Phone, iPhone and iPad, Android, and Mac OS/X - No link yet – still pending review by Apple store.
Note For additional information, see the Microsoft TechNet article Rights Management sharing application user guide.
This location is referenced during the Rights Management for Individuals signup flow, and more especially in the subsequent confirmation e-mail (see Section § Sharing protected content with anyone).
This cross-platform sharing application is also available through all the appropriate popular application stores, e.g. App Store, Google Play and Windows Store.
IT Professionals can download the installation packages (64-bit and 32-bit versions) of the Rights Management sharing application for Windows from the Microsoft download center for automatic deployment and thus make use of the ITPro-oriented silent setup options. The Windows version of the Rights Management sharing application indeed supports a scripted installation, which makes it suitable for enterprise deployments via the Azure Rights Management service preparation tool aadrmprep.exe.
Note For additional information, see the Microsoft TechNet article Rights Management sharing application administrator guide.
Note The Rights Management sharing application for Windows is not only reserved for those subscribing to the Microsoft Right Management cloud-hosted service offering but also available for organizations already using an AD RMS infrastructure on their premises.
Installing Rights Management sharing applications
To install a Rights Management sharing application on your computer or your device, proceed with the following steps:
- Open a browser session and navigate to the Microsoft Rights Management Download Center at https://portal.aadrm.com/Home/Download.

- Click the icon corresponding to your computer or device to download the related Microsoft Rights Management sharing application, for example the Windows blue icon for installation the sharing application for Windows. As indicated, support for additional devices is coming by October 2013.

- Click Run. An User Account Control dialog appears.
Note You must have administrative privileges for installing the sharing application on a computer. The AD RMS Client 2.1 is indeed installed as part of the sharing application installation package.
- Click Yes. A Setup Microsoft RMS wizard opens up.
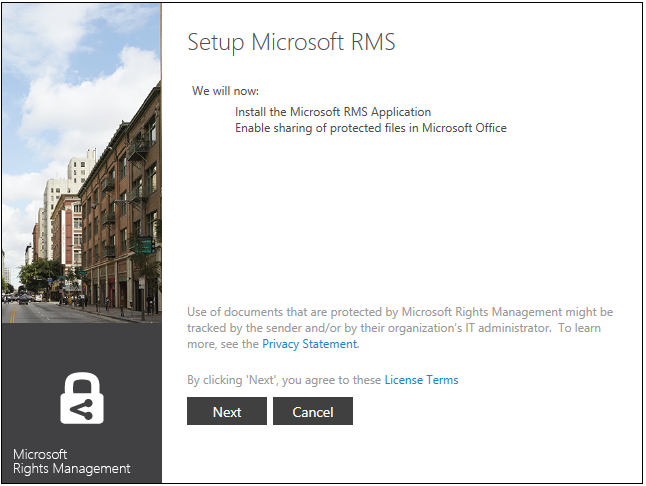
- Click Next.
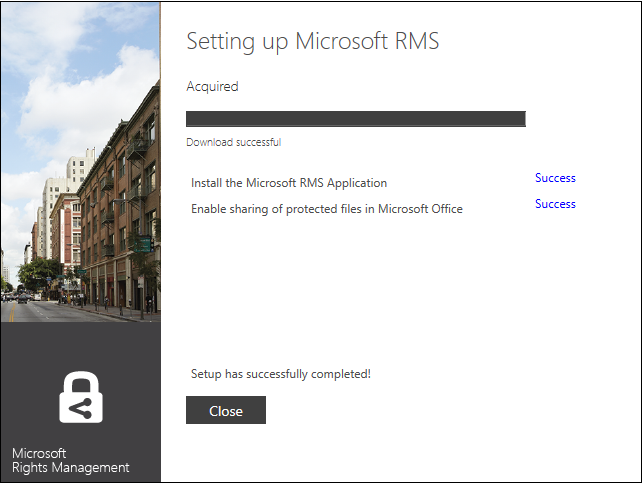
- When setup is finished, restart your computer to complete installation. Click Restart.
The setup experience is somehow similar on other devices whilst depending on the device.
Discovering Rights Management sharing applications for computers
On Windows computers, the Rights Management sharing application is available for computers running at least Windows 7 or newer version.
It provides the following capabilities:
- Protection of a single file or bulk protection of multiple files as well as all files within a selected folder:
- Native protection for PDF and Office documents, text and images files.
- Generic protection for any file type; especially useful for files and apps that do not support native Rights Management protection.
-
- Built-in viewer for commonly used text and image file types.
- Protection and sharing of any file with someone else (within or outside of your organization) via e-mail.
- Enhanced File Explorer (a.k.a. Windows Explorer in Windows 7 and above or Finder in Mac OS/X) by adding two items Protect in-place and Share Protected (see below).
- New buttons (Share Protected) added to the Microsoft Office Ribbon for Word, PowerPoint, and Excel applications, so that you can protect and share your files from within Office 2010 and Office 2013.
- Allows Office 2010 to work with the Azure Rights Management service by configuring automatically registry settings.
Protecting any type of document
The Rights Management sharing application is a user-driven application that helps protecting and consuming any file format. It uses the power of the File API, which supports automated protection and enhances the protection ecosystem by protecting all file formats.
The Rights Management sharing application for computers provides, depending of the level of integration possible with the file format, two different levels of protection:
- Native protection. This represents a strong level of protection that provides encryption and also application of a policy (enforcement of rights or permissions). Before opening a protected content, a successful authentication and authorization must occurred as depicted earlier in this document.
When authorization is granted, the content is rendered in accordance to the defined usage rights policy in RMS-enlightened applications (see Section § Leveraging the Microsoft RMS enlightened applications). In practice, the protected content is rendered in either the Microsoft Rights Management sharing application (for protected text and image files) or the associated application (for all other supported file formats):
- File format compatible with Rights Management protection keeps their original extension.
(For example, applying protection on a PDF file named Guide.pdf results in a protected PDF file with the same name Guide.pdf). The following file formats falls into this category: PDF, DOC, DOCX, XLS, XLSX, PPT, PTX and XPS files.
- Text and images get special treatment, the original file extension is appended with a P. (for example, TXT becomes PTXT, XML becomes PXML, JPG becomes PJPG… same behavior for PNG, JPEG TIFF, BMP, and GIF).
- Generic protection. This represents a good level of protection that provides encryption. The file is added to a Protected File (PFILE) container, which is then encrypted so that the file is protected, all from a stream based API.
Before protected content access is unlock, a user must be successful authenticated and authorized. When authorization is granted, the content is accessible and a central audit logging is also recorded by the Azure Rights Management service.
- When in-place protection is applied, original file extension is modified and becomes .EXT.PFILE. (For example a Visio document named MyDrawing.vsd becomes MyDrawing.vsd.pfile)
Note The Microsoft Rights Management sharing application is registered into the system to handle PFILE extension.
- Permissions are displayed but cannot be enforced once the file is opened in its original format (For example, once a VSD file is opened in Microsoft Visio). This enables any application to immediately participate in the RMS ecosystem.
Note The ability to protect natively or using the generic protection is configurable by an administrator.
Protecting a document from the File Explorer
The user can protect a document by using the Rights Management sharing application's integration in Windows and Mac OS/X, as well as via the Microsoft Office Ribbon extensions (see below). Generally stated, the capability is either:
- Protect in place. This flow will protect the file in place. The user can then take other actions to share the file, if need be. This flow is most suitable for personal or cloud-drive file protection flows. The user will be given the choice of protecting with an organizational RMS template, a previously saved user RMS template, or create a new ad-hoc template (see below).
-or-
- Share Protected: This flow will protect a copy of the selected file leaving the original file in its prior state (which could also be protected). This flow has the user addressing the document to people (e-mail addresses) and selecting related permissions. Upon sending, an unprotected e-mail will be sent with the protected document. The user can customize the e-mail before it is sent.
To protect in place a file from the Windows Explorer, proceed with the following steps:
- Right-click the file to protect in place and select protect in place, and then select a listed RMS template or select Custom Permissions…
- In the former case, the selected template is silently applied.
-or-
- In the latter case, an add protection dialog appears.
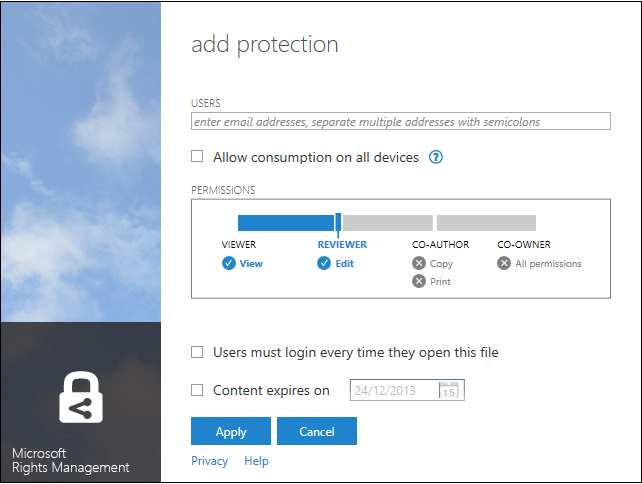
Set the slider to restrict Address and select the appropriate permissions (see below) and click Apply.
To share protected a file from the Windows Explorer, proceed with the following steps:
- Right-click the file to share protected and select share protected. A share protected dialog appears.
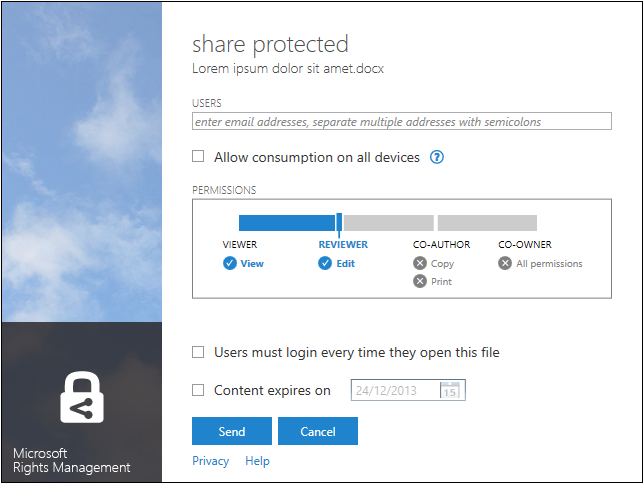
- Add the user(s) who will be able to access the file in USERS.
- Optionally select Allow consumption on all devices if the file will be shared with users who use devices such as iOS and Android. In this case, the sharing application adds the file to a container which is then encrypted so that the file is protected. This mode will thus allow them to view the file on their devices (and even using device-specific applications like Pages on an iPad) after the sharing application on the device verifies they have access to the file.
- Set the slider in PERMISSIONS to restrict with the appropriate permissions what the recipient(s) of the file will be able to do (see below) and click Send. An Outlook 2013 I have securely shared file(s) with you dialog opens up. An e-mail has been created that is ready to be sent but you can edit it first

An e-mail has been created that is ready to be sent but you can edit it first. The recipient(s) can view the file, and can simply sign up for a free Microsoft Rights Management account as needed (see Section § Sharing protected content with anyone).
Protecting and sharing a document from within Office 2010 and Office 2013
As previously outlined, the Rights Management sharing application for Windows add a Share Protected button on the Microsoft Office Ribbon, which enables to share a protected copy of the document with others. Related Rights Management add-ins for Excel, PowerPoint and Word are stored in the following folder: C:\Program Files (x86)\Microsoft RMS Office Addins.
To protect and share a document from Word 2013, for example, proceed with the following steps:
- From Word 2013, save the document.
- Click Share Protected for sharing a sensitive file.
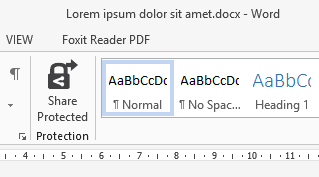
A share protected dialog appears.

- Address and select the appropriate permissions (see below) and click Send. An Outlook 2013 I have securely shared file(s) with you dialog opens up. An e-mail has been created that is ready to be sent but you can edit it first

An e-mail has been created that is ready to be sent but you can edit it first. The recipient(s) can view the file, and can simply sign up for a free Rights Management account as needed (see Section § Sharing protected content with anyone).
Using RMS Templates
The general use of RMS templates enables an organization to define and implement information policies that are consistent across the organization. When implementing automatic rules leveraging RMS templates, then protection applies to everybody in the company across the board.
Templates reduce the effort of determining who should be assigned user rights and what types of rights the intended consumer should receive from the publisher. Furthermore, when modifications to a template occur, all past, present, and future content based on that template will inherit the new rights when a use license is issued.
If the feature that requires a new use license with every access is used with a template, the organization can dynamically change rights policies after the document is published or sent by e-mail. This way, the organization retains the option to further restrict or loosen control on one or more users at any time.
Azure Rights Management service's administrators design and control the content of the templates. They can easily modify the template definitions of approved consumers and the rights that are assigned to those users within a rights-protected document.
Important note The Azure Rights Management service contains by default two templates built-in. At the time of this writing, the capability to create additional templates is not yet present.
The last and up-to-date version of a RMS template resides in the Cloud and is always used when a use license is created so that the most recent policy set by the Microsoft RMS administrator is enforced. Each RMS client must download the templates that it will use.
These local versions of the templates do not need to be updated every time the Azure Rights Management service's administrator updates the template, because the Azure Rights Management service's tenant uses its own copy when it evaluates the rights that the template specifies. However, templates still must be available locally for a user to select them when he or she performs offline publishing, as it's the case for Office applications.
Note If the AD RMS Client 2.1 is bootstrapped against an AD RMS on-premises installation, then the Microsoft Rights Management sharing application will show the on-premises templates.
Using Custom RMS permissions
As seen previously, with RMS templates, it's quick and easy to apply protection on documents that are only access by people working inside the organization. Whenever you want to collaborate with other organizations or with individuals outside, you will share protected documents by applying custom RMS permissions. Custom RMS permission allows to grant people access (individuals inside or outside the organization) on a protected document while controlling their ability to use the document (for example edit, copy, or print).

With the Rights Management sharing application, a document owner can apply permissions to a file through customized combinations of permissions assigned to each specified individual identified with corresponding e-mail address.
Below is a description of supported Rights Management permissions along with their definitions:
| Permission | Description |
| Allow consumption on all devices | Mobile devices users will need to install the Microsoft Rights Management sharing application to view the protected file. The file is added to a container which is then encrypted so that the file is protected. The sharing application on the device verifies that users have access to the file and then allows them to view the file on their devices (and even using device-specific applications like Pages on an iPad). |
| Users must login every time they open this file | This right sets the use license to expire immediately after the protected content has been accessed. As a result, the consumer must have online access to the Azure Rights Management service to get another use license every time the document is opened. |
| Content expires on
| This right expires the consumer's ability to open a protected document at a date that the publisher set. Please note that:
|
Below is a description of various Rights Management roles along with their definition.
| Role | Permission(s) |
| Viewer | View: this right enables the consumer to read a protected document but not print, edit, save, or copy. |
| Reviewer | View and Edit Edit: this right enables the consumer to modify a protected document but not print or copy. |
| Co-author | View, Edit, Copy and Print Copy: This right enables the consumer to copy content of a protected document to the clipboard. Print: this right enables the consumer to print protected content. If this right is not assigned, the user cannot print the document, even if he or she can open it and view it. |
| Co-owner | All Permissions This right gives the consumer the same abilities that the publisher has. This right acts as if no rights restrictions have been applied. It is typically enabled only for an individual who is a member of a larger group of consumers for whom rights that are more restrictive have been applied. It can also be used to transfer ownership of a document. |
Discovering Microsoft Rights Management sharing applications for devices
The Microsoft Rights Management sharing application for mobile devices provides the following capabilities:
- Open generic protected files shared by other.
- Built-in viewer for commonly used text and image file types.
- Create protected images from the camera or on-device camera roll. This can be seen as the "secure whiteboard" feature: take a photo of the meeting room whiteboard and share it with all attendees, securely.
Note Although the Microsoft Rights Management sharing application can send protected document by e-mail, only the attached document is protected leaving the body of e-mail unencrypted. The main purpose of the "share protected" functionality is for secure collaborating with others that don't have yet sign up with the Azure Rights Management service. The e-mail contains instruction for sign up for Microsoft Rights Management for free.
Sharing with others protected images from an iPad
More and more information workers use their mobile device for capturing information when taking for example a photo of the meeting room whiteboard.
One new feature, exclusively available on the Microsoft Rights Management sharing application for mobile devices, is the ability for users to create protected images from the camera or on-device camera roll and share it with other attendees, securely.
To illustrate the feature on an iPad, proceed with the following steps:
- Launch the Microsoft Rights Management sharing application for iOS by taping the RMS sharing application.
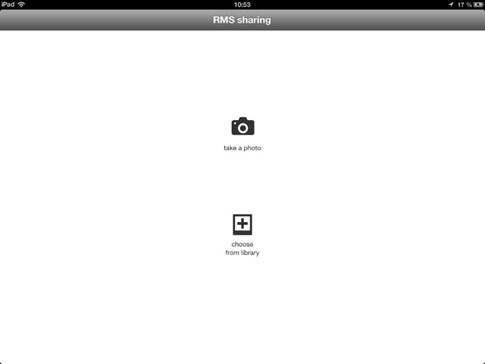
- Tap take a photo or choose from library to pick a picture from Camera Roll.

- If the photography is correct, tap Use.

- Enter the credentials of your organizational account and tap Sign in.
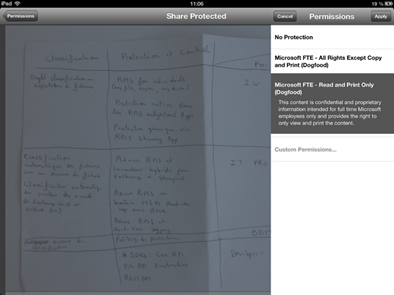
- The list of available templates is display, you can choose the Read and Print Only one or tap Custom Permissions…
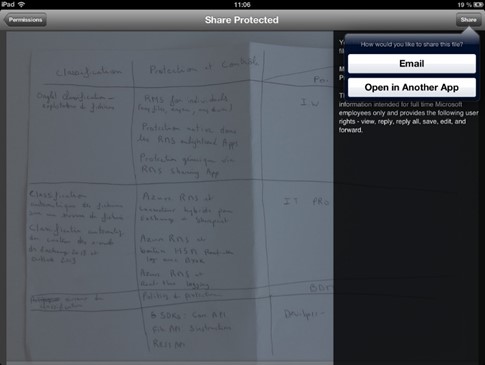
- To share with others, tap Email.
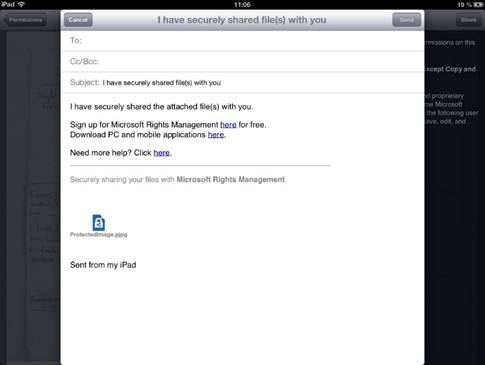
- An -email is automatically generated for you, containing the protected image file and instructions for recipients that don't have signed up for the Microsoft Rights Management sharing application. Add the recipients e-mail address and tap "Send".
Opening protected files shared by others on an iPad
Here's another example of how it works when a user receives an e-mail with a protected document:
- When he launches the protected document, the Rights Management sharing application contacts the Azure Rights Management service to get a use license.
- The Azure Rights Management service redirects the user to authenticate against the Windows Azure AD.
- Based on the user's e-mail address, the Azure Rights Management service looks up in the Windows Azure AD tenant (Microsoft Rights Management for individuals or Cloud identities) or redirects to the local on-premises federation infrastructure, e.g. AD FS for instance, to validate the credentials (federated identities).
- Once the user's credentials are validated, the Azure Rights Management service then controls that the user is authorized to access this document. If an access should be granted, the Azure Rights Management service then sends back to the Microsoft Rights Management sharing application an appropriate use license.
When downloading or opening a protected file, the file association on the device displays the icon of the Rights Management sharing application provided that the Rights Management sharing application is already installed on that device.
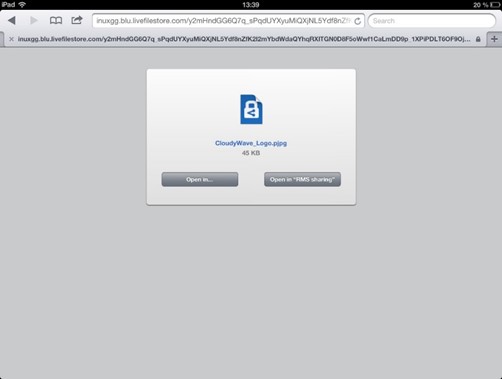
Furthermore, when downloading a protected file by using the browser (as illustrated hereafter with the .pjpg extension), you can directly open the file with the Rights Management sharing application by simply clicking Open in "RMS sharing".
The protected image file is then opened and rendered in the Rights Management sharing application and the associated information policy is displayed. In this case, authorized users are only allow to view and print the content.
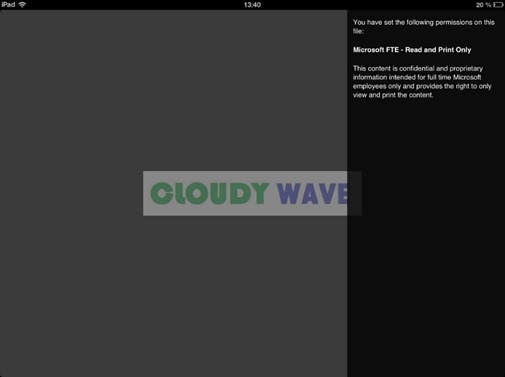
Sharing protected content with anyone
Users expect to be able to collaborate with anyone by sharing their documents. Often, this usually means emailing a document by attaching it without additional controls. Thus, people tend to conceptualize sharing as sending. Microsoft Rights Management sharing applications make it easy to share document with other individuals in a secure way by e-mailing the protected document.
Note RMS-enlightened applications can also offer in-built file sharing capabilities.
By controlling access to information based on user identity, the Azure Rights Management service is a solution that safeguard corporate information. When access is granted and information is unlocked, the Azure Rights Management service also provides rich auditing capabilities.
To ease the collaboration beyond your organization's boundaries and beyond the organizations that subscribed to the Azure Rights Management service – where the collaboration between them constitutes a native feature as covered earlier in this document, the Azure Rights Management service provides new ways for individuals and/or users in organizations that don't offer the Azure Rights Management service to their employees individuals to sign up for a free account.
With the free Microsoft Rights Management for individuals, users can share with anyone (any business user or any individual), even those who don't have subscribed to Azure Rights Management service as part of Office 365 or as a stand-alone service.
In order to securely consume or exchange protected files, anyone can now follow these three easy steps:
- Signing up for a free Microsoft Rights Management account via a simple registration experience.
- Installing the Microsoft Rights Management sharing application.
- Open received protected files or protect any file or any folder with the Share Protected feature.
To sign up for a free account, proceed with the following steps:
- Open a browser session and navigate to the Microsoft Rights Management portal.
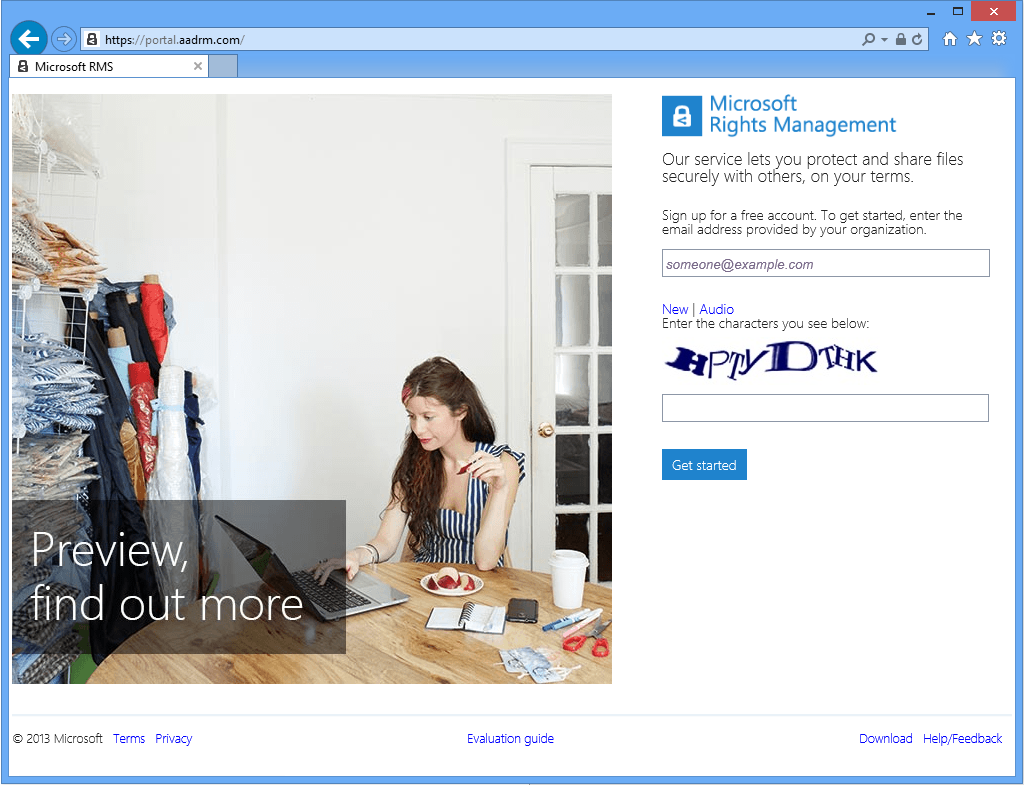
- Specify your organizational/personal e-mail address you want to use to sign in, for example "alice@contoso-corporation" and type the characters corresponding to the displayed CAPTCHA.
- Click Get started. At this stage, several checks are made before an ad-hoc Rights Management service account is created. In particular, the Azure Rights Management service checks to see if the parent organization already has a Windows Azure AD tenant, if the user already had an account, etc.
Note A Windows Azure AD tenant is provisioned if the user's organization doesn't already have one.
A Rights Management for Individuals ad-hoc account is simply a Windows Azure AD tenant that is created for a specific organization (not shared across organizations) and the user account is added. There is no administrator for these tenants. If other users from the same organization create ad-hoc accounts, they are placed in this same headless tenant. By way of (this) example, alice@contoso-coporation.com signs up. The tenant CONTOSO-CORPORATION is cre ated. Alice's user account is added to the tenant CONTOSO-CORPORATION. Alice's account is given the Microsoft Rights Management for individuals SKU. bob@contoso-coporation.com signs up. The tenant CONTOSO-CORPORATION exists and is reused. Bob's user account is added to the tenant CONTOSO-CORPORATION. Bob's account is given the Microsoft Rights Management for individuals SKU.
IT professionals will be given the ability to convert these ad-hoc accounts to licensed users with no impact to the user or the tenant. Once this is done, IT professionals will have full management capabilities for these users.
If the various checks succeed, a verification e-mail is sent to the email address you've provided to validate your ownership of the email address.
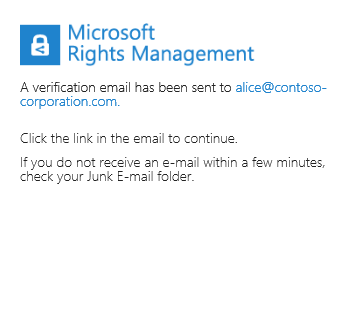
- Open your favorite e-mail client/Webmail application.
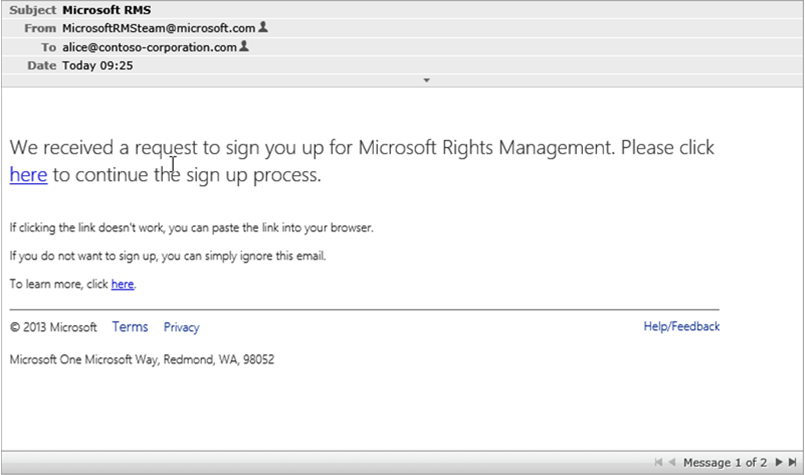
- Check your inbox for a mail entitled Microsoft RMS from MicrosoftRMSteam@microsoft.com and follow its instructions.
- Click the link here provided in the above e-mail. Once your ownership is proven, a new Microsoft RMS tab opens up in the browser.
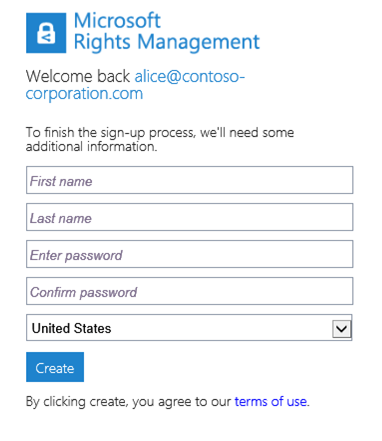
- To complete the signup process, specify your first name and your last name, enter a password, confirm it, select a country in the dropdown box and password, and then click Create to provision the account. The self-service Rights Management for individuals' accounts will be re-validated on a monthly basis.
- The account is being provisioned. When the sign up process is finished, a confirmation e-mail is sent to your address. Wait a few minutes before checking your e-mails.

- You should receive a new email also entitled Microsoft RMS from MicrosoftRMSteam@microsoft.com that confirms the completion of the sign up process.
- Click the first link here to download the Microsoft Rights Management sharing application. A new Microsoft RMS tab opens up in the browser with the Download section of the Microsoft Rights Management portal.
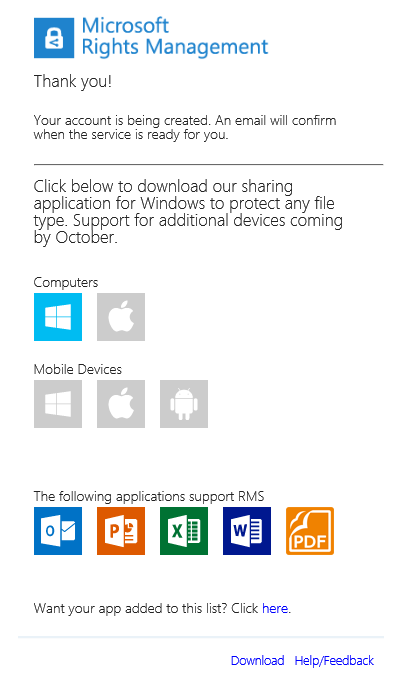
You can now install the sharing application for your device and start leveraging the Azure Rights Management service as an individual.